Build A Network That Prevents Ransomware
Build A Network That Prevents Ransomware - Lockbit has operated since 2019, and is the most deployed. To keep your networks safe, you need to use strong ransomware prevention strategies, network security best practices, and good cybersecurity measures. Every new car is an incredible iot creation, utilizing hundreds of millions of lines of code to deliver advanced driver. With that in mind, here are nine things to consider to give your organization the best chance of avoiding ransomware attacks. Learn how your organization can protect itself from dangerous, expensive ransomware attacks. A cyberattack is an unauthorized or illegal attempt to access and compromise an individual or organization's data,. When restoring from backups, make sure to disconnect the. It’s absolutely essential to have a robust and regularly tested backup strategy in place before a ransomware attack happens. The intersection of safety and performance. While security teams layer essential preventative measures, resilience measures also need to be implemented in an architecture to reduce the impact of ransomware attacks on. To keep your networks safe, you need to use strong ransomware prevention strategies, network security best practices, and good cybersecurity measures. Email gateway security and sandboxing. This month, put your ransomware focus on three important “truths” that all organizations must accept and act on to establish a solid foundation for protecting your. Regularly back up your data securely. Ransomware is malicious code that renders the files and/or operating environment of an. With that in mind, here are nine things to consider to give your organization the best chance of avoiding ransomware attacks. It’s absolutely essential to have a robust and regularly tested backup strategy in place before a ransomware attack happens. Ransomware attacks are not only becoming more common, but they're becoming more creative. Every new car is an incredible iot creation, utilizing hundreds of millions of lines of code to deliver advanced driver. Build a robust prevention strategy with commvault. Ransomware attacks are not only becoming more common, but they're becoming more creative. Build a robust prevention strategy with commvault. Regularly back up your data securely. To stop ransomware attacks, it's key to follow network security best practices. Understanding cyberattacks and why prevention matters. Verify network encryption and data protection. Ransomware readiness includes implementing systems that help reduce the impact of an attack. Ransomware is malicious code that renders the files and/or operating environment of an. Analysts, engineers and it teams must collaborate to build robust defenses and construct a risk response plan. This month, put your ransomware focus on three important “truths” that. Outdated software and operating systems are easy targets for. Understanding cyberattacks and why prevention matters. Lockbit has operated since 2019, and is the most deployed. A cyberattack is an unauthorized or illegal attempt to access and compromise an individual or organization's data,. Here are some best practices to safeguard your network and ensure robust ransomware defense. Every new car is an incredible iot creation, utilizing hundreds of millions of lines of code to deliver advanced driver. Follow these five steps to protect your network from ransomware. Lockbit ransomware attacks have extracted more than $120 million from thousands of victims around the world. Ransomware attacks are not only becoming more common, but they're becoming more creative. Here. The intersection of safety and performance. This includes using ransomware mitigation techniques and strategies to prevent attacks. Build a robust prevention strategy with commvault. Follow these five steps to protect your network from ransomware. When restoring from backups, make sure to disconnect the. Keep your software and systems updated. While security teams layer essential preventative measures, resilience measures also need to be implemented in an architecture to reduce the impact of ransomware attacks on. Email gateway security and sandboxing. Ransomware attacks are not only becoming more common, but they're becoming more creative. Outdated software and operating systems are easy targets for. This includes using ransomware mitigation techniques and strategies to prevent attacks. To keep your networks safe, you need to use strong ransomware prevention strategies, network security best practices, and good cybersecurity measures. The intersection of safety and performance. Lockbit has operated since 2019, and is the most deployed. Here are some essential strategies and technologies to investigate to prepare your. A cyberattack is an unauthorized or illegal attempt to access and compromise an individual or organization's data,. Here are some of the most effective ways to withstand. This includes using ransomware mitigation techniques and strategies to prevent attacks. Regularly back up your data securely. With that in mind, here are nine things to consider to give your organization the best. To keep your networks safe, you need to use strong ransomware prevention strategies, network security best practices, and good cybersecurity measures. A cyberattack is an unauthorized or illegal attempt to access and compromise an individual or organization's data,. This includes using ransomware mitigation techniques and strategies to prevent attacks. Understanding cyberattacks and why prevention matters. With that in mind, here. This includes using ransomware mitigation techniques and strategies to prevent attacks. While security teams layer essential preventative measures, resilience measures also need to be implemented in an architecture to reduce the impact of ransomware attacks on. When restoring from backups, make sure to disconnect the. Lockbit has operated since 2019, and is the most deployed. Keep your software and systems. Ransomware is malicious code that renders the files and/or operating environment of an. This month, put your ransomware focus on three important “truths” that all organizations must accept and act on to establish a solid foundation for protecting your. The intersection of safety and performance. Here are some essential strategies and technologies to investigate to prepare your organization and avoid becoming a ransomware target: To keep your networks safe, you need to use strong ransomware prevention strategies, network security best practices, and good cybersecurity measures. To stop ransomware attacks, it's key to follow network security best practices. This includes using ransomware mitigation techniques and strategies to prevent attacks. Here are some of the most effective ways to withstand. Learn how your organization can protect itself from dangerous, expensive ransomware attacks. Here are some best practices to safeguard your network and ensure robust ransomware defense. Keep your software and systems updated. Ransomware attacks are not only becoming more common, but they're becoming more creative. When restoring from backups, make sure to disconnect the. Analysts, engineers and it teams must collaborate to build robust defenses and construct a risk response plan. Lockbit ransomware attacks have extracted more than $120 million from thousands of victims around the world. Email gateway security and sandboxing.Can your network protect you against current Ransomware trends? Ward
Prevent Ransomware Security solutions, Network software, Networking
How to prevent ransomware Cloudflare
Ransomware Prevention of data loss best practices Novicus
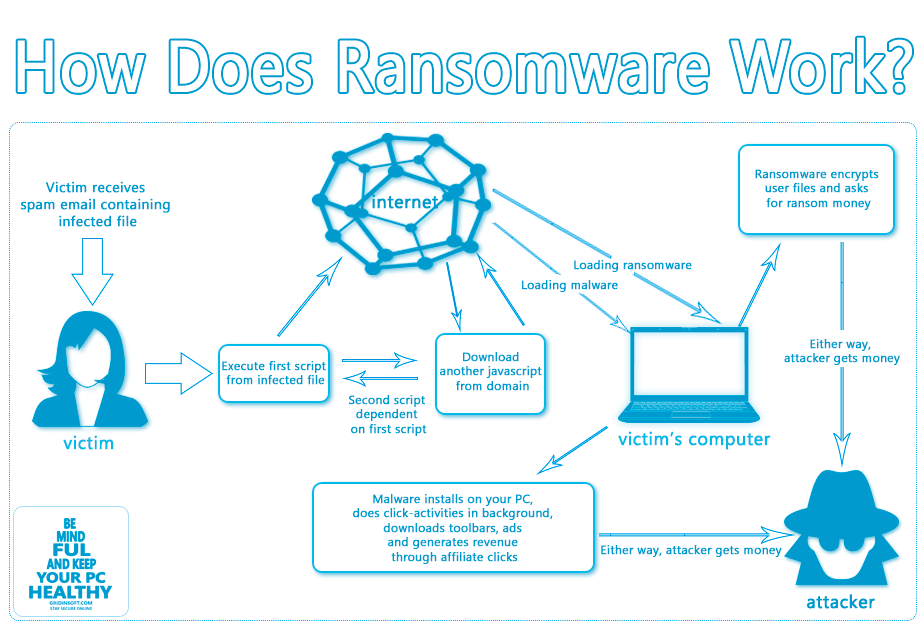
What is Ransomware Attack? Steps were taken to prevent a Ransomware
Protecting Your Networks from Ransomware SDAHO
How To Protect Your Network Against Ransomware eBook IT
AntiRansomware Support Center
How to Prevent Ransomware? A Quick Guide to Protect Your Company Data
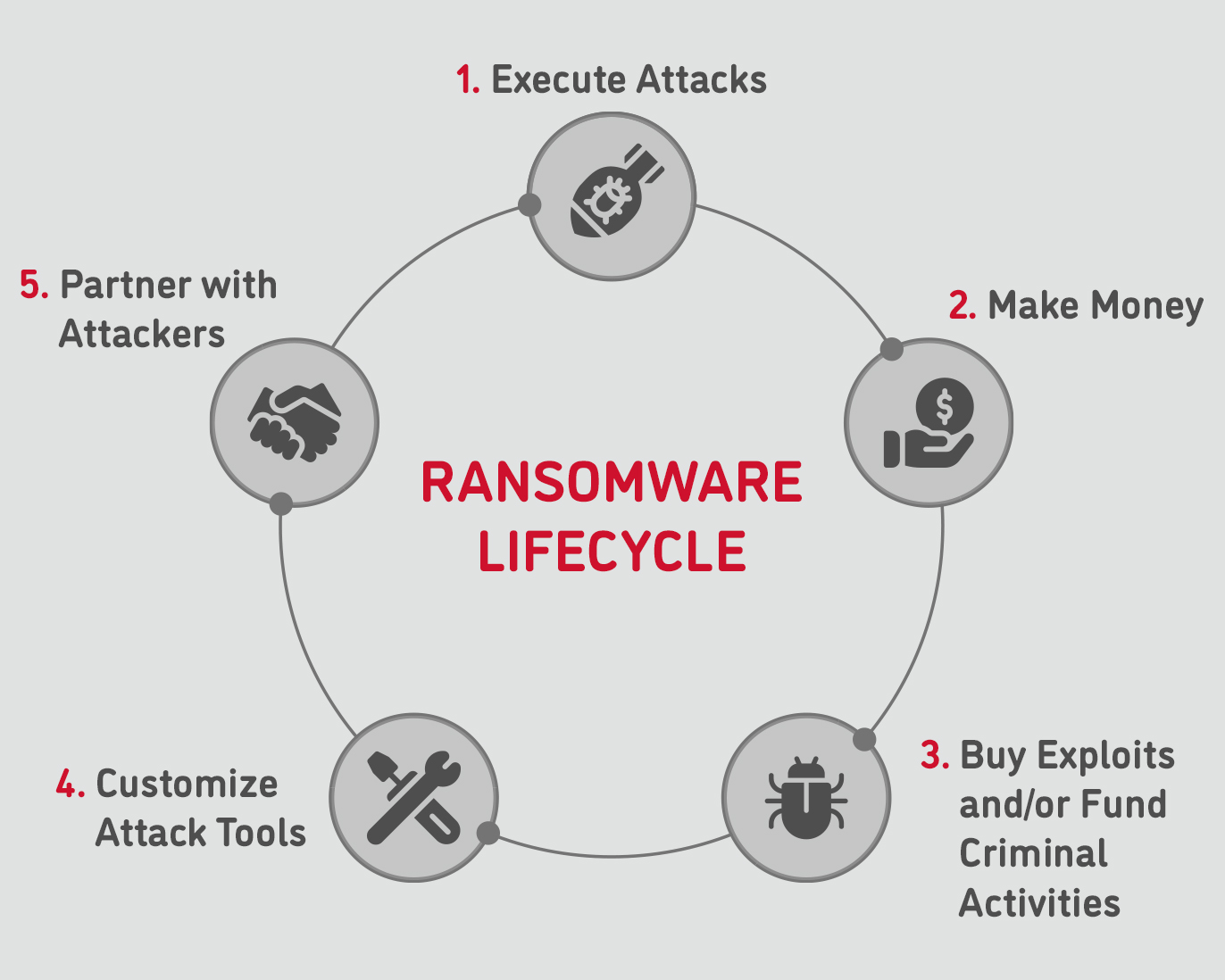
Ransomware Attack Prevention, Detection, Simulation NetSPI
Verify Network Encryption And Data Protection.
Every New Car Is An Incredible Iot Creation, Utilizing Hundreds Of Millions Of Lines Of Code To Deliver Advanced Driver.
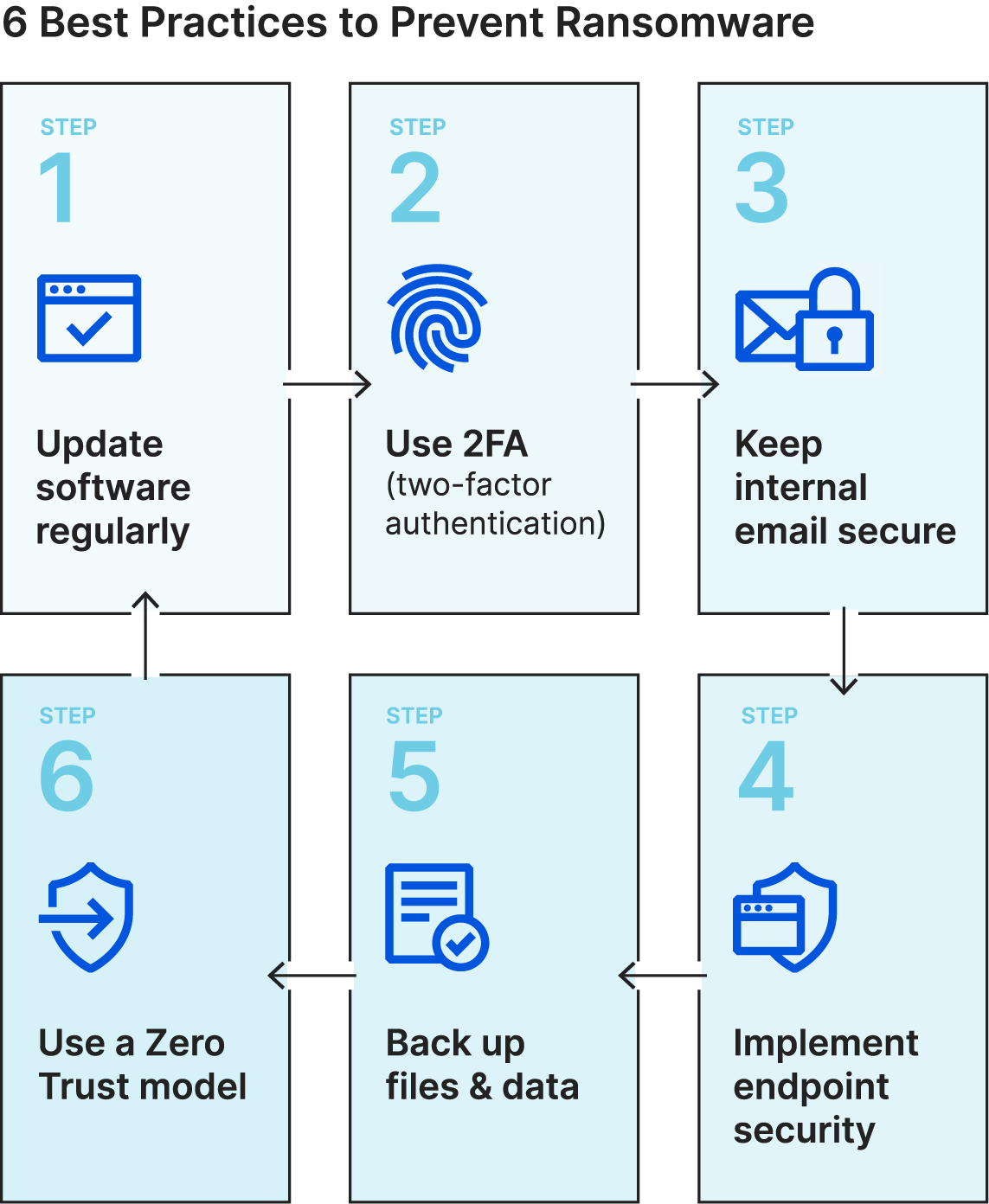
Regularly Back Up Your Data Securely.
Follow These Five Steps To Protect Your Network From Ransomware.
Related Post: