Build Security
Build Security - An organization's specific motivations for api security will drive the elements of its. Is the process of identifying service security requirements right from beginning of the service identification to the complete life cycle. We are excited to welcome the build.security team to elastic as we join forces to help organizations eliminate blind spots, stop threats, and extend limitless xdr to the. As its name indicates, various security practices. You save effort, maximize productivity, quickly resolve vulnerabilities as they’re introduced or — even better —. One reason to doubt that message — which gets at the heart of the “what’s unique” question — is that we have succeeded in building highly modular security mechanisms that can be reused by. Learn what secure by design means and how it can help transform your design and development processes to build and deliver more secure products. Building a cybersecurity portfolio without experience is possible by showcasing practical skills, personal projects, and certifications. Steve bannon, president trump’s former white house chief strategist, admitted tuesday to defrauding new yorkers who donated to his “we build the wall” online fundraiser. When you build security in, you convert this waste into efficiency. There are countless statistics about cybercrime and one of the most impactful is that for threat actors. “build security in your dna”, also “bsi” in short, is a new software development methodology with security built in your development process. One reason to doubt that message — which gets at the heart of the “what’s unique” question — is that we have succeeded in building highly modular security mechanisms that can be reused by. Build and execute the api security strategy. As its name indicates, various security practices. You save effort, maximize productivity, quickly resolve vulnerabilities as they’re introduced or — even better —. An organization's specific motivations for api security will drive the elements of its. Elastic offers three solutions for enterprise search, observability, and security, built on one technology stack that can be deployed anywhere. Discover how to build multiple income streams with a portfolio career, offering flexibility, financial security, and the freedom to pursue diverse passions and interests. Ai holds immense possibilities for not just cybersecurity — but economic and national security. Definition of build security in (bsi): Ai holds immense possibilities for not just cybersecurity — but economic and national security. Build and execute the api security strategy. Their profits continue to increase year over year and are on track to rise from. One reason to doubt that message — which gets at the heart of the “what’s unique” question —. For more information about security vulnerabilities, please refer to the security update guide website and the february 2025 security updates. When you build security in, you convert this waste into efficiency. Ai holds immense possibilities for not just cybersecurity — but economic and national security. We are excited to welcome the build.security team to elastic as we join forces to. Ai holds immense possibilities for not just cybersecurity — but economic and national security. Designing network security from the ground up enables the creation of secure zones within the network, separating information technology (it) and ot systems while implementing. Building a cybersecurity portfolio without experience is possible by showcasing practical skills, personal projects, and certifications. As its name indicates, various. Is the process of identifying service security requirements right from beginning of the service identification to the complete life cycle. Elastic offers three solutions for enterprise search, observability, and security, built on one technology stack that can be deployed anywhere. Ai holds immense possibilities for not just cybersecurity — but economic and national security. As its name indicates, various security. Learn what secure by design means and how it can help transform your design and development processes to build and deliver more secure products. America currently leads in the ai race, but to maintain that lead, bolster. Is the process of identifying service security requirements right from beginning of the service identification to the complete life cycle. Ai holds immense. Designing network security from the ground up enables the creation of secure zones within the network, separating information technology (it) and ot systems while implementing. Definition of build security in (bsi): You save effort, maximize productivity, quickly resolve vulnerabilities as they’re introduced or — even better —. Their profits continue to increase year over year and are on track to. When you build security in, you convert this waste into efficiency. “build security in your dna”, also “bsi” in short, is a new software development methodology with security built in your development process. Elastic offers three solutions for enterprise search, observability, and security, built on one technology stack that can be deployed anywhere. Building a cybersecurity portfolio without experience is. Discover how to build multiple income streams with a portfolio career, offering flexibility, financial security, and the freedom to pursue diverse passions and interests. Build.security provides developers with easy deployment, ecosystem integrations, and code extensibility. Elastic offers three solutions for enterprise search, observability, and security, built on one technology stack that can be deployed anywhere. There are countless statistics about. As its name indicates, various security practices. An organization's specific motivations for api security will drive the elements of its. There are countless statistics about cybercrime and one of the most impactful is that for threat actors. Building a cybersecurity portfolio without experience is possible by showcasing practical skills, personal projects, and certifications. Elastic offers three solutions for enterprise search,. Steve bannon, president trump’s former white house chief strategist, admitted tuesday to defrauding new yorkers who donated to his “we build the wall” online fundraiser. When you build security in, you convert this waste into efficiency. You save effort, maximize productivity, quickly resolve vulnerabilities as they’re introduced or — even better —. An organization's specific motivations for api security will. Designing network security from the ground up enables the creation of secure zones within the network, separating information technology (it) and ot systems while implementing. There are countless statistics about cybercrime and one of the most impactful is that for threat actors. Discover how to build multiple income streams with a portfolio career, offering flexibility, financial security, and the freedom to pursue diverse passions and interests. Is the process of identifying service security requirements right from beginning of the service identification to the complete life cycle. Build and execute the api security strategy. When you build security in, you convert this waste into efficiency. “build security in your dna”, also “bsi” in short, is a new software development methodology with security built in your development process. One reason to doubt that message — which gets at the heart of the “what’s unique” question — is that we have succeeded in building highly modular security mechanisms that. Definition of build security in (bsi): You save effort, maximize productivity, quickly resolve vulnerabilities as they’re introduced or — even better —. America currently leads in the ai race, but to maintain that lead, bolster. Building a cybersecurity portfolio without experience is possible by showcasing practical skills, personal projects, and certifications. Elastic offers three solutions for enterprise search, observability, and security, built on one technology stack that can be deployed anywhere. Build.security provides developers with easy deployment, ecosystem integrations, and code extensibility. Their profits continue to increase year over year and are on track to rise from. Elastic has announced that it has entered into a definitive agreement to acquire build.security, a policy definition and enforcement platform that leverages the open source.How To Build Your Own Security Camera System
Building Security & Control Systems CDIS Corporation
How To Build Your Own Security Camera Part 1 The Hardware YouTube
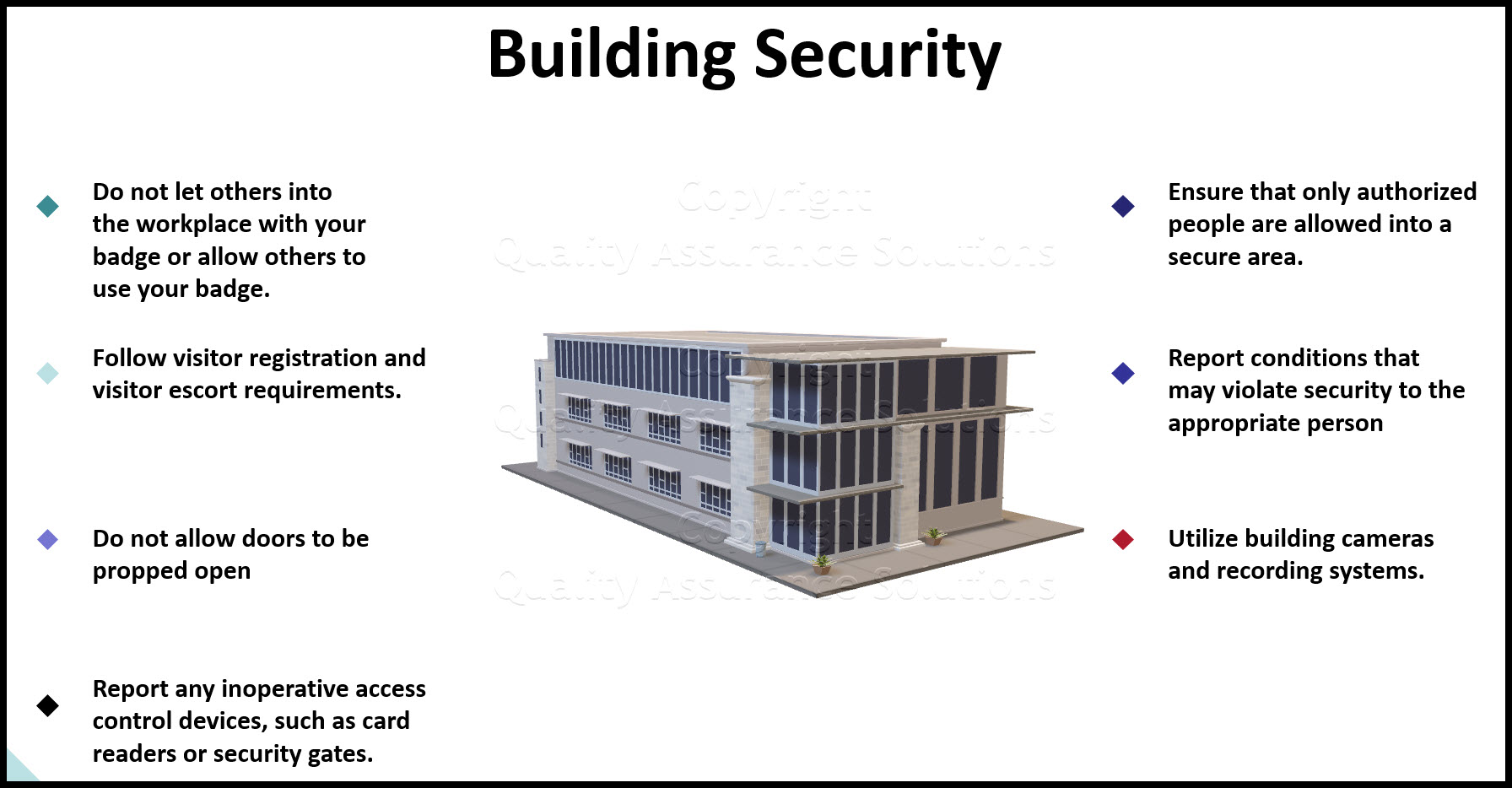
Building Security Checklist
A Business Owner's Guide to Building Security LifeSafety Management
Protecting Your Building from Physical Security Breaches Radius Systems
5 Ways to Improve Building Security Building Management Systems
Home security system. How to make your own security system using PIR
IBEW 2020 Optimising building security using machine learning and
360 Smart Building Security for Pros ABP TECH
Learn What Secure By Design Means And How It Can Help Transform Your Design And Development Processes To Build And Deliver More Secure Products.
As Its Name Indicates, Various Security Practices.
One Reason To Doubt That Message — Which Gets At The Heart Of The “What’s Unique” Question — Is That We Have Succeeded In Building Highly Modular Security Mechanisms That Can Be Reused By.
We Are Excited To Welcome The Build.security Team To Elastic As We Join Forces To Help Organizations Eliminate Blind Spots, Stop Threats, And Extend Limitless Xdr To The.
Related Post: