Building A Soc
Building A Soc - Building a soc requires many considerations; Five major steps are involved in developing a soc: No facility is the same—even when two identical buildings are built, their different locations, functions,. It’s time for a reality check: Socs act as the front line to your cybersecurity efforts. Building a fully fledged soc from scratch is a major challenge. With the increasing number of cyber. Bartlett city aldermen in a 5 to 1 vote denied the permit of a mosque for the bartlett muslim society. Soc metrics can be used to show how the center is improving overall security, meeting objectives, and reducing risk exposure. The tools and techniques outlined in this post can help you get started on building your soc as you assemble your security team, plan their workload and coordinate their. What does it actually take? In this article, i will cover the roadmap of soc, planning and building strategies, developing use cases, team building planning, sop (standard operating process), sow. Soc 1 reports are primarily used by auditors and financial professionals, while soc 2 and soc 3 reports cater to a broader audience interested in security and privacy. The city of bartlett board of mayor and alderman on tuesday night. Building a modest infosec (information security) program — much less a 24/7 soc — is a challenging. A simpler approach is to start small and then build on this in a slow and controlled manner to create a fully fledged soc. Bartlett city aldermen in a 5 to 1 vote denied the permit of a mosque for the bartlett muslim society. Proper planning will enable you to effectively monitor threats, respond swiftly when an attack occurs, and maintain secure. Building a fully fledged soc from scratch is a major challenge. Step one of creating a soc is determining if there’s a clear need for one. It’s time for a reality check: Sans defines them as “a combination of people, processes and technologies protecting the information systems of an. A soc is an effective facility for monitoring business information security and digital threats. What does it actually take? Building a security operations center (soc) from scratch is a formidable task, one that requires careful planning, resource. In this article, we will walk you through the bits and pieces of building a soc. Building a security operations center (soc) from scratch is a formidable task, one that requires careful planning, resource allocation, and implementation. In this article, i will cover the roadmap of soc, planning and building strategies, developing use cases, team building planning, sop (standard operating. Soc metrics can be used to show how the center is improving overall security, meeting objectives, and reducing risk exposure. The city of bartlett board of mayor and alderman on tuesday night. In this article, we will walk you through the bits and pieces of building a soc. A simpler approach is to start small and then build on this. Bartlett city aldermen in a 5 to 1 vote denied the permit of a mosque for the bartlett muslim society. Proper planning will enable you to effectively monitor threats, respond swiftly when an attack occurs, and maintain secure. Building a modest infosec (information security) program — much less a 24/7 soc — is a challenging. It’s time for a reality. Five major steps are involved in developing a soc: Building a security operations center (soc) from scratch is a formidable task, one that requires careful planning, resource allocation, and implementation. In this article, we will walk you through the bits and pieces of building a soc. Building a fully fledged soc from scratch is a major challenge. Soc metrics can. Socs act as the front line to your cybersecurity efforts. Soc metrics can be used to show how the center is improving overall security, meeting objectives, and reducing risk exposure. It’s time for a reality check: Five major steps are involved in developing a soc: Building a fully fledged soc from scratch is a major challenge. Building a successful security operations centre (soc) can greatly enhance the ability to detect and disrupt cyber attacks, protecting the business from harm. Five major steps are involved in developing a soc: Step one of creating a soc is determining if there’s a clear need for one. Building a security operations center (soc) from scratch is a formidable task, one. Socs act as the front line to your cybersecurity efforts. The tools and techniques outlined in this post can help you get started on building your soc as you assemble your security team, plan their workload and coordinate their. A simpler approach is to start small and then build on this in a slow and controlled manner to create a. In this article, i will cover the roadmap of soc, planning and building strategies, developing use cases, team building planning, sop (standard operating process), sow. Building a fully fledged soc from scratch is a major challenge. With the increasing number of cyber. In this article, we will walk you through the bits and pieces of building a soc. Building a. Learn about six key tips on how to establish the right mindset before building a security operations center (soc)—a critical first step for security leaders. The tools and techniques outlined in this post can help you get started on building your soc as you assemble your security team, plan their workload and coordinate their. Socs act as the front line. Building a soc requires many considerations; Five major steps are involved in developing a soc: Soc 1 reports are primarily used by auditors and financial professionals, while soc 2 and soc 3 reports cater to a broader audience interested in security and privacy. Building a security operations center (soc) from scratch is a formidable task, one that requires careful planning, resource allocation, and implementation. What does it actually take? Learn about six key tips on how to establish the right mindset before building a security operations center (soc)—a critical first step for security leaders. A soc is an effective facility for monitoring business information security and digital threats. It’s time for a reality check: Bartlett city aldermen in a 5 to 1 vote denied the permit of a mosque for the bartlett muslim society. Proper planning will enable you to effectively monitor threats, respond swiftly when an attack occurs, and maintain secure. Building a fully fledged soc from scratch is a major challenge. Sans defines them as “a combination of people, processes and technologies protecting the information systems of an. The tools and techniques outlined in this post can help you get started on building your soc as you assemble your security team, plan their workload and coordinate their. No facility is the same—even when two identical buildings are built, their different locations, functions,. A simpler approach is to start small and then build on this in a slow and controlled manner to create a fully fledged soc. With the increasing number of cyber.7 Steps to Build a SOC with Limited Resources PPT
Best Practices for Building a SOC Team (SOC)
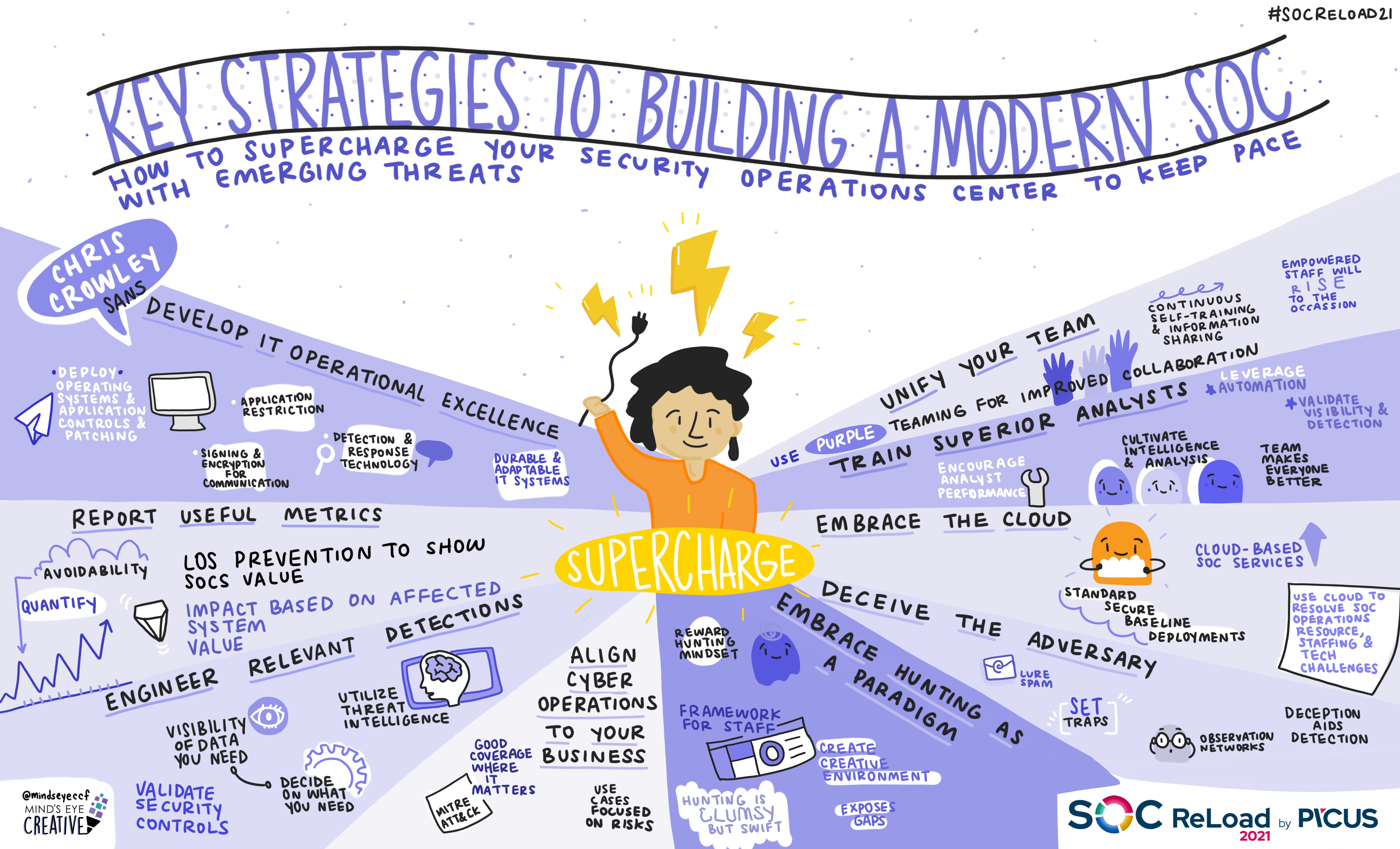
How to Build a Modern SOC in 2024? SOCReLoad Conference
SOLUTION How to build a soc Studypool
Building a SOC 7 Best Practices to Consider Hurricane Labs
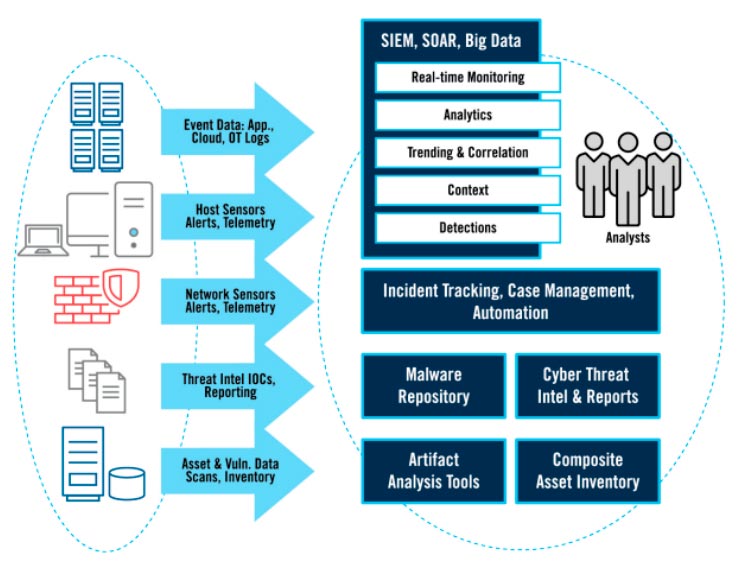
Building a Security Operations Center (SOC) From Scratch SOC
DTS Solution Building a SOC (Security Operations Center) PPT
7 Steps to Building a Security Operations Center
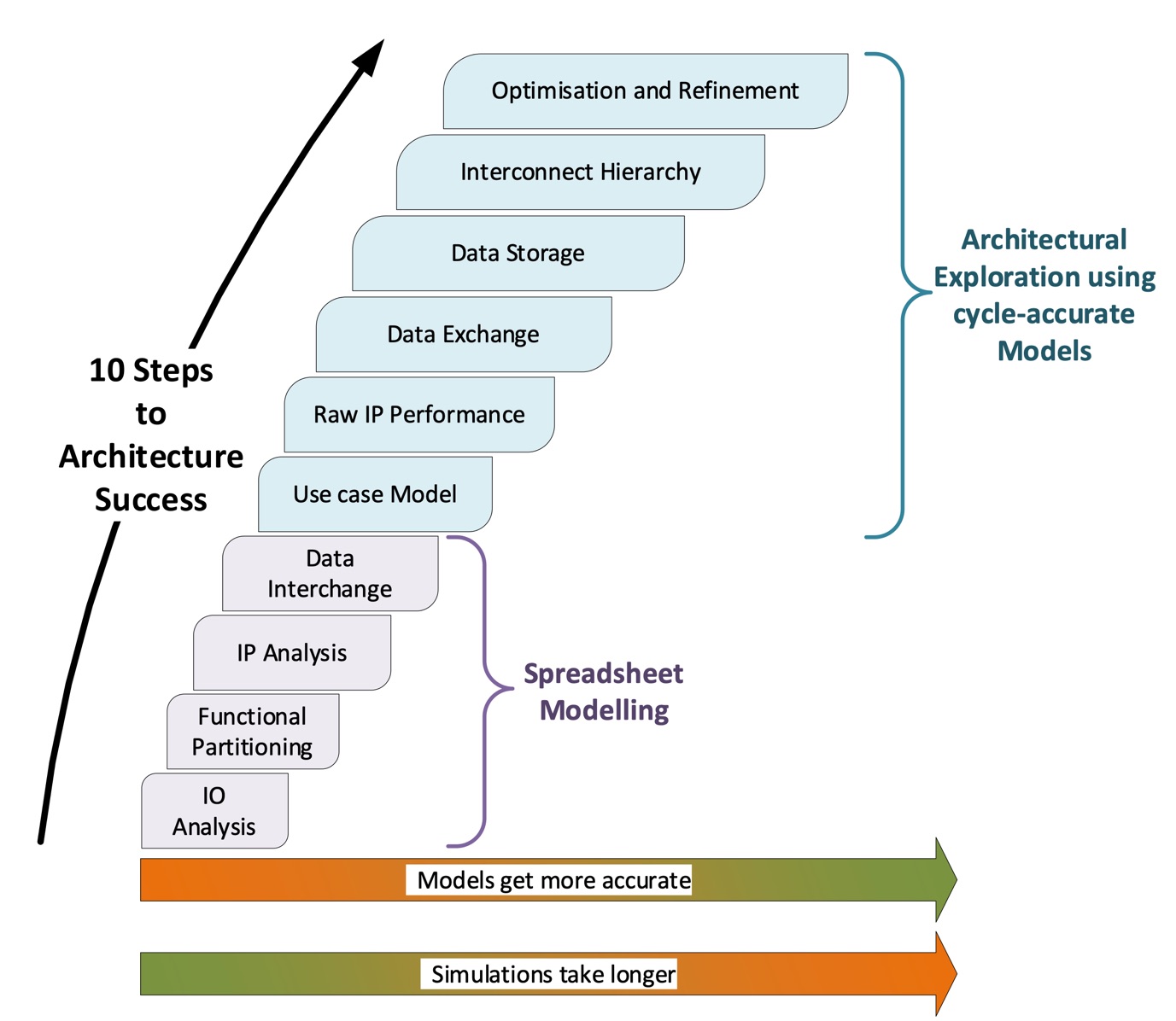
Ten steps to designing an SoC
7 Steps to Build a SOC with Limited Resources PPT
Building A Successful Security Operations Centre (Soc) Can Greatly Enhance The Ability To Detect And Disrupt Cyber Attacks, Protecting The Business From Harm.
Socs Act As The Front Line To Your Cybersecurity Efforts.
The City Of Bartlett Board Of Mayor And Alderman On Tuesday Night.
In This Article, We Will Walk You Through The Bits And Pieces Of Building A Soc.
Related Post: