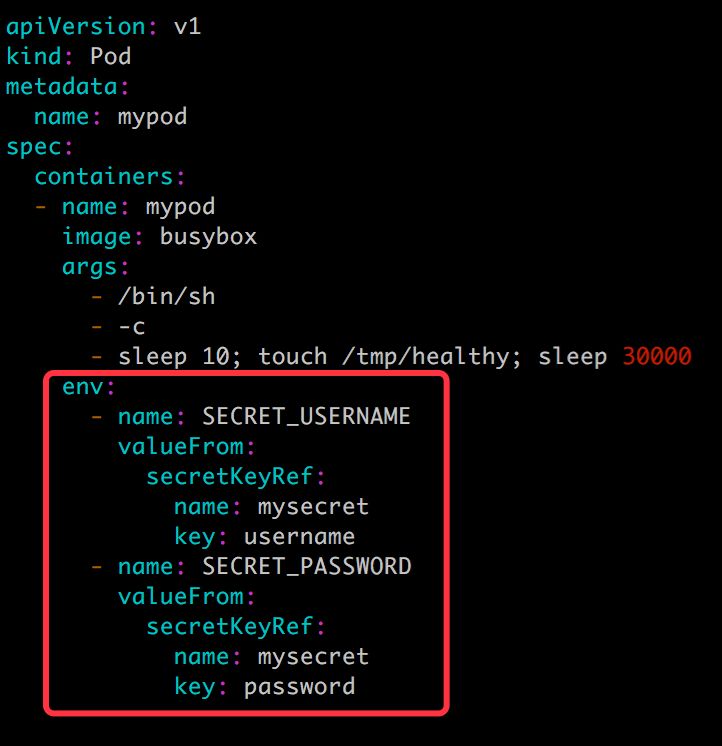
Docker Build Secret
Docker Build Secret - Mount a volume at build time, use it in a run. Docker build supports two forms of secrets: Learn how to use the secret mount type to access private data during your docker builds without leaving traces in the image. In your local repository on your machine, run the following command. When you’re building a docker image, you might need to use some secrets: Docker 18.09 added some nice build enhancements, including a feature called build secrets, that help us solve just this. I want to use the env type like this: To use build secrets you’ll first need. Add the pat as a repository secret in your github repository, with the name dockerhub_token. This github repository provides examples of how to configure the linux emulator as part of a github actions ci workflow for.net, python, java and go applications. You don’t want this secret to end up. Build secrets implementation is based on two new features provided by buildkit. Managing secrets in docker involves avoiding common pitfalls like embedding them in dockerfiles or source code. Docker build supports two forms of secrets: When you’re building a docker image, you might need to use some secrets: Docker 18.09 added some nice build enhancements, including a feature called build secrets, that help us solve just this. In your local repository on your machine, run the following command. Mount a volume at build time, use it in a run. In terms of docker swarm services, a secret is a blob of data, such as a password, ssh private key, ssl certificate, or another piece of data that should not be transmitted over a network or. One is the ability to use custom builder frontends loaded from images in the registry, and the. First you need to pass the secret into the docker build command, and then you need to consume the secret in. Learn how to use the secret mount type to access private data during your docker builds without leaving traces in the image. This article explains the benefits and limitations of this feature,. A build secret is sensitive information, such. Secret mounts add secrets as files. Build secrets implementation is based on two new features provided by buildkit. Learn how to use the secret mount type to access private data during your docker builds without leaving traces in the image. A build secret is sensitive information, such as a password or api token, consumed as part of the build process.. I want to use the env type like this: Docker build supports two forms of secrets: First you need to pass the secret into the docker build command, and then you need to consume the secret in. Managing secrets in docker involves avoiding common pitfalls like embedding them in dockerfiles or source code. Build secrets implementation is based on two. I want to use the env type like this: First you need to pass the secret into the docker build command, and then you need to consume the secret in. Docker 18.09 added some nice build enhancements, including a feature called build secrets, that help us solve just this. Docker build supports two forms of secrets: In your local repository. You don’t want this secret to end up. In your local repository on your machine, run the following command. Secret mounts add secrets as files. In terms of docker swarm services, a secret is a blob of data, such as a password, ssh private key, ssl certificate, or another piece of data that should not be transmitted over a network. Mount a volume at build time, use it in a run. A build secret is sensitive information, such as a password or api token, consumed as part of the build process. Managing secrets in docker involves avoiding common pitfalls like embedding them in dockerfiles or source code. This article explains the benefits and limitations of this feature,. Learn how to. To use build secrets you’ll first need. Mount a volume at build time, use it in a run. When you’re building a docker image, you might need to use some secrets: You don’t want this secret to end up. Docker build supports two forms of secrets: This github repository provides examples of how to configure the linux emulator as part of a github actions ci workflow for.net, python, java and go applications. I want to use the env type like this: Managing secrets in docker involves avoiding common pitfalls like embedding them in dockerfiles or source code. Docker build supports two forms of secrets: In terms. In your local repository on your machine, run the following command. Build secrets implementation is based on two new features provided by buildkit. This github repository provides examples of how to configure the linux emulator as part of a github actions ci workflow for.net, python, java and go applications. Buildkit introduces a secure mechanism for managing secrets during the docker. When you’re building a docker image, you might need to use some secrets: You don’t want this secret to end up. Docker build supports two forms of secrets: In your local repository on your machine, run the following command. A build secret is sensitive information, such as a password or api token, consumed as part of the build process. Managing secrets in docker involves avoiding common pitfalls like embedding them in dockerfiles or source code. In terms of docker swarm services, a secret is a blob of data, such as a password, ssh private key, ssl certificate, or another piece of data that should not be transmitted over a network or. This article explains the benefits and limitations of this feature,. First you need to pass the secret into the docker build command, and then you need to consume the secret in. To use build secrets you’ll first need. When you’re building a docker image, you might need to use some secrets: Docker build supports two forms of secrets: Learn how to use the secret mount type to access private data during your docker builds without leaving traces in the image. Buildkit introduces a secure mechanism for managing secrets during the docker image build process, ensuring that critical information, such as api keys and credentials, is. In your local repository on your machine, run the following command. Mount a volume at build time, use it in a run. Add the pat as a repository secret in your github repository, with the name dockerhub_token. Secret mounts add secrets as files. The password to a private package repository, for example. You don’t want this secret to end up. I want to use the env type like this:Run docker on secret ninelasopa
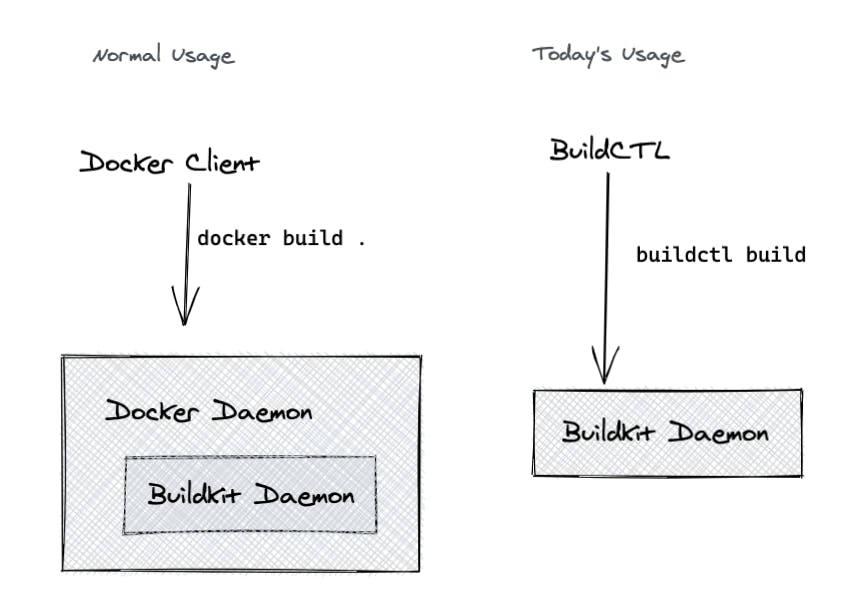
BuildKit & Docker Buildx
Support for docker build secret for buildtime docker secrets
How to mount secret file in docker image build & use variable from
The Complete Guide to Docker Secrets Earthly Blog
环境变量方式使用 Secret 每天5分钟玩转 Docker 容器技术(158) 墨天轮
GitHub hnakamur/dockerbuildsecretexample An example for using
How to Handle Secrets in Docker Security Boulevard
How to create and use a Docker secret from a file YouTube
Dockerイメージビルド時の秘密情報の扱い方に関するまとめ
Docker 18.09 Added Some Nice Build Enhancements, Including A Feature Called Build Secrets, That Help Us Solve Just This.
This Github Repository Provides Examples Of How To Configure The Linux Emulator As Part Of A Github Actions Ci Workflow For.net, Python, Java And Go Applications.
A Build Secret Is Sensitive Information, Such As A Password Or Api Token, Consumed As Part Of The Build Process.
Build Secrets Implementation Is Based On Two New Features Provided By Buildkit.
Related Post: