Docker Build Secrets
Docker Build Secrets - You can use docker's secret management feature to mount a secret file in a docker image build and use a variable from the secret file in the dockerfile to authenticate a. Docker 18.09 added some nice build enhancements, including a feature called build secrets, that help us solve just this. Mount a volume at build time, use it in a run. See examples of how to specify secrets from files and how. Docker build supports two forms of secrets: If you develop a container that can be deployed as a service and requires sensitive data, such as a credential, as an environment. A build secret is any piece of sensitive information, such as a password or api token, consumed as part of your application's build process. Buildkit introduces a secure mechanism for managing secrets during the docker image build process, ensuring that critical information, such as api keys and credentials, is. The password to a private package repository, for example. Build arguments and environment variables are. When you’re building a docker image, you might need to use some secrets: Build support for docker secrets into your images. The source of a secret can be. If you develop a container that can be deployed as a service and requires sensitive data, such as a credential, as an environment. You can use docker's secret management feature to mount a secret file in a docker image build and use a variable from the secret file in the dockerfile to authenticate a. Build arguments and environment variables are. Docker build supports two forms of secrets: This github repository provides examples of how to configure the linux emulator as part of a github actions ci workflow for.net, python, java and go applications. I want to use the env type like this: Learn how to use docker buildkit's secret mount type to access private data during your build without leaving traces in the image. You don’t want this secret to end up. Build arguments and environment variables are. The source of a secret can be. Learn how to use docker buildkit's secret mount type to access private data during your build without leaving traces in the image. Build support for docker secrets into your images. Learn how to use docker buildkit's secret mount type to access private data during your build without leaving traces in the image. A build secret is sensitive information, such as a password or api token, consumed as part of the build process. Docker 18.09 added some nice build enhancements, including a feature called build secrets, that help us solve just. Mount a volume at build time, use it in a run. To use build secrets you’ll first need. The password to a private package repository, for example. Build support for docker secrets into your images. I want to use the env type like this: The source of a secret can be. To use build secrets you’ll first need. A build secret is sensitive information, such as a password or api token, consumed as part of the build process. Mount a volume at build time, use it in a run. I want to use the env type like this: Mount a volume at build time, use it in a run. Secret mounts add secrets as files. Build support for docker secrets into your images. When you’re building a docker image, you might need to use some secrets: Build arguments and environment variables are. Mount a volume at build time, use it in a run. See examples of how to specify secrets from files and how. Buildkit introduces a secure mechanism for managing secrets during the docker image build process, ensuring that critical information, such as api keys and credentials, is. I want to use the env type like this: If you develop a. You don’t want this secret to end up. I want to use the env type like this: Build arguments and environment variables are. The source of a secret can be. Learn how to use docker buildkit's secret mount type to access private data during your build without leaving traces in the image. To use build secrets you’ll first need. Learn how to use docker buildkit's secret mount type to access private data during your build without leaving traces in the image. This github repository provides examples of how to configure the linux emulator as part of a github actions ci workflow for.net, python, java and go applications. A build secret is any. Mount a volume at build time, use it in a run. This github repository provides examples of how to configure the linux emulator as part of a github actions ci workflow for.net, python, java and go applications. Learn how to use docker buildkit's secret mount type to access private data during your build without leaving traces in the image. Secret. Mount a volume at build time, use it in a run. The source of a secret can be. Buildkit introduces a secure mechanism for managing secrets during the docker image build process, ensuring that critical information, such as api keys and credentials, is. Build arguments and environment variables are. The password to a private package repository, for example. Docker 18.09 added some nice build enhancements, including a feature called build secrets, that help us solve just this. Mount a volume at build time, use it in a run. Build arguments and environment variables are. When you’re building a docker image, you might need to use some secrets: If you develop a container that can be deployed as a service and requires sensitive data, such as a credential, as an environment. The source of a secret can be. To use build secrets you’ll first need. Learn how to use docker buildkit's secret mount type to access private data during your build without leaving traces in the image. The password to a private package repository, for example. This github repository provides examples of how to configure the linux emulator as part of a github actions ci workflow for.net, python, java and go applications. You don’t want this secret to end up. A build secret is any piece of sensitive information, such as a password or api token, consumed as part of your application's build process. A build secret is sensitive information, such as a password or api token, consumed as part of the build process. Secret mounts add secrets as files. Docker build supports two forms of secrets: Buildkit introduces a secure mechanism for managing secrets during the docker image build process, ensuring that critical information, such as api keys and credentials, is.Python Docker Build How to Install Private Artifactory Modules
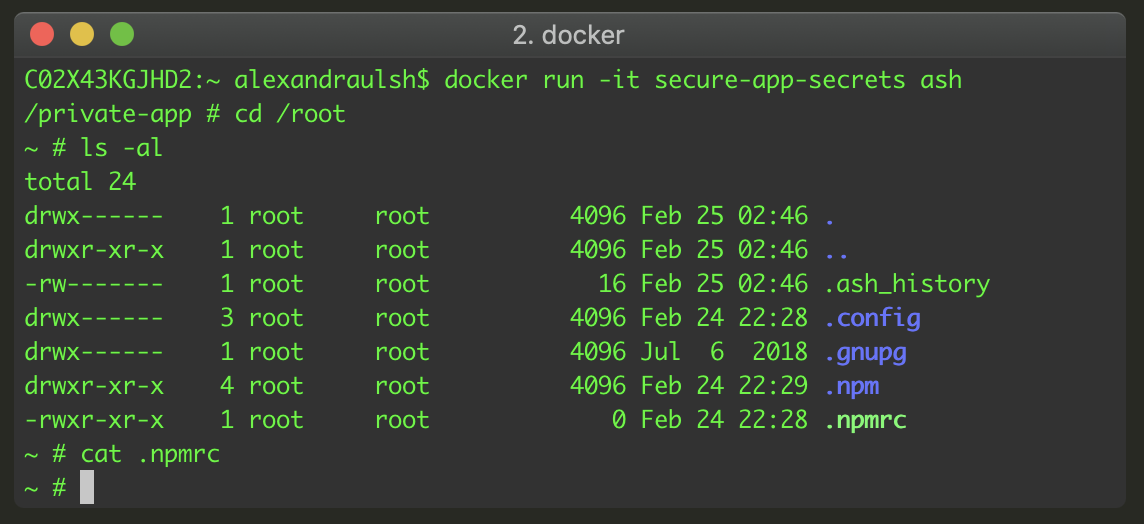
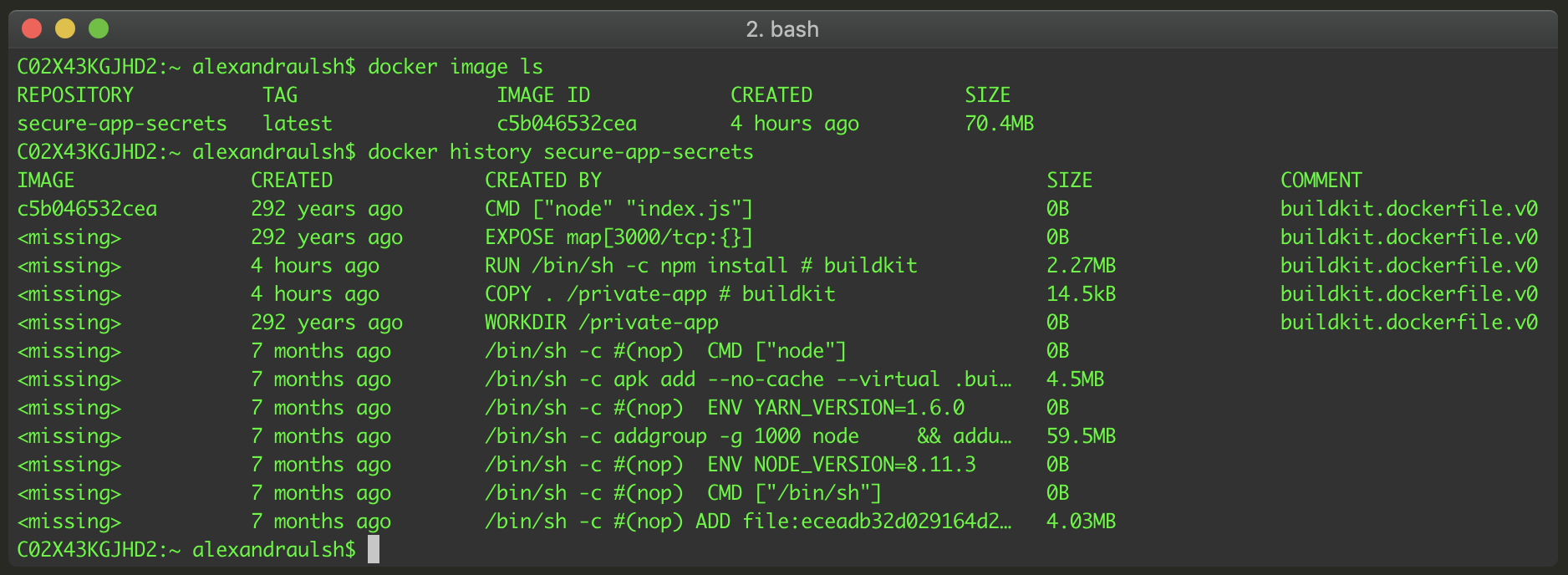
Docker build secrets and private npm packages Alexandra Ulsh
The Complete Guide to Docker Secrets Earthly Blog
Docker build secrets first impressions Omoroi
Unlock the Secrets of Docker Image Creation! StepbyStep Guide Inside
Build secrets and SSH forwarding in Docker 18.09 by Tõnis Tiigi Medium
The Complete Guide to Docker Secrets Earthly Blog
Docker build secrets and private npm packages Alexandra Ulsh
How to Handle Secrets in Docker Security Boulevard
GitHub hnakamur/dockerbuildsecretexample An example for using
Build Support For Docker Secrets Into Your Images.
I Want To Use The Env Type Like This:
See Examples Of How To Specify Secrets From Files And How.
You Can Use Docker's Secret Management Feature To Mount A Secret File In A Docker Image Build And Use A Variable From The Secret File In The Dockerfile To Authenticate A.
Related Post: