How To Build A Firewall
How To Build A Firewall - Good firewall policy has three primary sections: You also do this visibly, meaning that most every rule you write will log when traffic hits it. By implementing a firewall, you can create a secure and controlled network environment, ensuring the confidentiality, integrity, and availability of your data. What are the system requirements for. In this article, we will explore how to build a hardware firewall from scratch, including the necessary components, configurations, and best practices to ensure a secure network. I'll show you both physical and virtual installation steps, as well as general advice that can be used for a. Learn how to create an effective firewall to protect your network against cyber threats with our comprehensive guide. It is not a new video, but is one of the best i. Setting up a firewall is the first step in securing your network. To complement our tutorial video above, this article will walk you. Configuring a firewall can be an intimidating project, but breaking down the work into simpler tasks can make the work much more manageable. It is not a new video, but is one of the best i. By implementing a firewall, you can create a secure and controlled network environment, ensuring the confidentiality, integrity, and availability of your data. To complement our tutorial video above, this article will walk you. You also do this visibly, meaning that most every rule you write will log when traffic hits it. Learn how to create an effective firewall to protect your network against cyber threats with our comprehensive guide. If you have ever thought about building your own firewall/router, but have yet to actually do it, here is a great guide that explains it. In this guide, we’ll unravel how to set up a firewall and some critical factors to consider while doing so. A successful firewall setup and deployment requires careful design, implementation, and maintenance to effectively. Whether you’re setting up a new network or upgrading your security measures, deploying a new firewall is a pivotal step. We present a basic guide that should help you configure a firewall in simple steps, including activities like creating zones, configuring settings, testing the configuration, managing the. The commands are run as the “__openconfig” user (which has the device administrator role) on the firewall. You also do this visibly, meaning that most every rule you write will log when traffic. Learn how to create an effective firewall to protect your network against cyber threats with our comprehensive guide. You can greatly reduce the risk of this issue by restricting. In this guide, we’ll unravel how to set up a firewall and some critical factors to consider while doing so. It is not a new video, but is one of the. Configuring a firewall can be an intimidating project, but breaking down the work into simpler tasks can make the work much more manageable. To complement our tutorial video above, this article will walk you. You can greatly reduce the risk of this issue by restricting. If you have ever thought about building your own firewall/router, but have yet to actually. By implementing a firewall, you can create a secure and controlled network environment, ensuring the confidentiality, integrity, and availability of your data. You can greatly reduce the risk of this issue by restricting. I'll show you both physical and virtual installation steps, as well as general advice that can be used for a. Good firewall policy has three primary sections:. Today we're building a firewall using sophos xg. You can greatly reduce the risk of this issue by restricting. If you have ever thought about building your own firewall/router, but have yet to actually do it, here is a great guide that explains it. The commands are run as the “__openconfig” user (which has the device administrator role) on the. If you have ever thought about building your own firewall/router, but have yet to actually do it, here is a great guide that explains it. Whether you’re setting up a new network or upgrading your security measures, deploying a new firewall is a pivotal step. You also do this visibly, meaning that most every rule you write will log when. Configuring a firewall involves various components—from hardware. Configuring a firewall can be an intimidating project, but breaking down the work into simpler tasks can make the work much more manageable. You can greatly reduce the risk of this issue by restricting. You also do this visibly, meaning that most every rule you write will log when traffic hits it. Learn. Learn how to create an effective firewall to protect your network against cyber threats with our comprehensive guide. In this article, we delve into the intricacies of firewall construction, exploring the key aspects that contribute to its effectiveness and reliability. In this article, we will explore how to build a hardware firewall from scratch, including the necessary components, configurations, and. Today we're building a firewall using sophos xg. A successful firewall setup and deployment requires careful design, implementation, and maintenance to effectively. In this article, we will explore how to build a hardware firewall from scratch, including the necessary components, configurations, and best practices to ensure a secure network. Configuring a firewall can be an intimidating project, but breaking down. Learn how to create an effective firewall to protect your network against cyber threats with our comprehensive guide. In this guide, we’ll unravel how to set up a firewall and some critical factors to consider while doing so. A successful firewall setup and deployment requires careful design, implementation, and maintenance to effectively. We present a basic guide that should help. In this guide, we’ll unravel how to set up a firewall and some critical factors to consider while doing so. By implementing a firewall, you can create a secure and controlled network environment, ensuring the confidentiality, integrity, and availability of your data. What are the system requirements for. We present a basic guide that should help you configure a firewall in simple steps, including activities like creating zones, configuring settings, testing the configuration, managing the. Configuring a firewall can be an intimidating project, but breaking down the work into simpler tasks can make the work much more manageable. It is not a new video, but is one of the best i. Learn how to create an effective firewall to protect your network against cyber threats with our comprehensive guide. You also do this visibly, meaning that most every rule you write will log when traffic hits it. Setting up a firewall is the first step in securing your network. Today we're building a firewall using sophos xg. I'll show you both physical and virtual installation steps, as well as general advice that can be used for a. If you have ever thought about building your own firewall/router, but have yet to actually do it, here is a great guide that explains it. The commands are run as the “__openconfig” user (which has the device administrator role) on the firewall. Whether you’re setting up a new network or upgrading your security measures, deploying a new firewall is a pivotal step. In this article, we delve into the intricacies of firewall construction, exploring the key aspects that contribute to its effectiveness and reliability. You can greatly reduce the risk of this issue by restricting.Build a NextGeneration Firewall for less than 100 Building an
Build Your Own Firewall Step by Step
How to Build a Firewall
5 WAYS TO CREATE A SECURE FIREWALL Adviacent
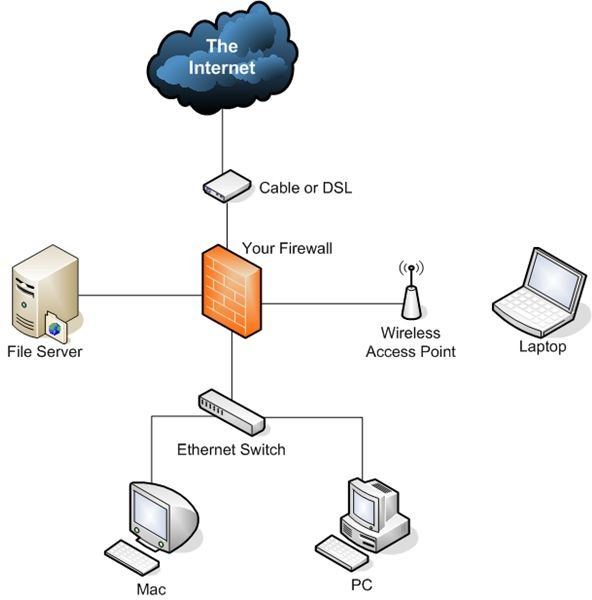
Classic firewall installation. Download Scientific Diagram
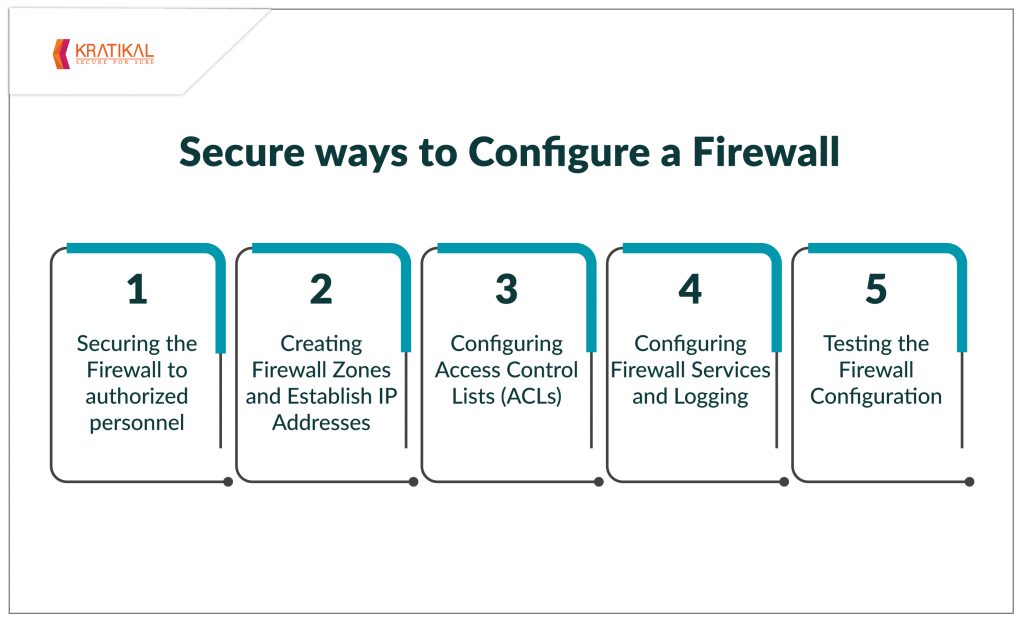
5 secure ways to configure a Firewall Security Boulevard
🔴 How to Create Firewall Rules in the Windows Firewall YouTube
How To Build Firewall Temporaryatmosphere32
How To Build A Human Firewall In 5 Steps
How to Build Firewall with Zima and 2.5GbE Intel NIC? ZimaBoard
In This Article, We Will Explore How To Build A Hardware Firewall From Scratch, Including The Necessary Components, Configurations, And Best Practices To Ensure A Secure Network.
Good Firewall Policy Has Three Primary Sections:
A Successful Firewall Setup And Deployment Requires Careful Design, Implementation, And Maintenance To Effectively.
To Complement Our Tutorial Video Above, This Article Will Walk You.
Related Post: