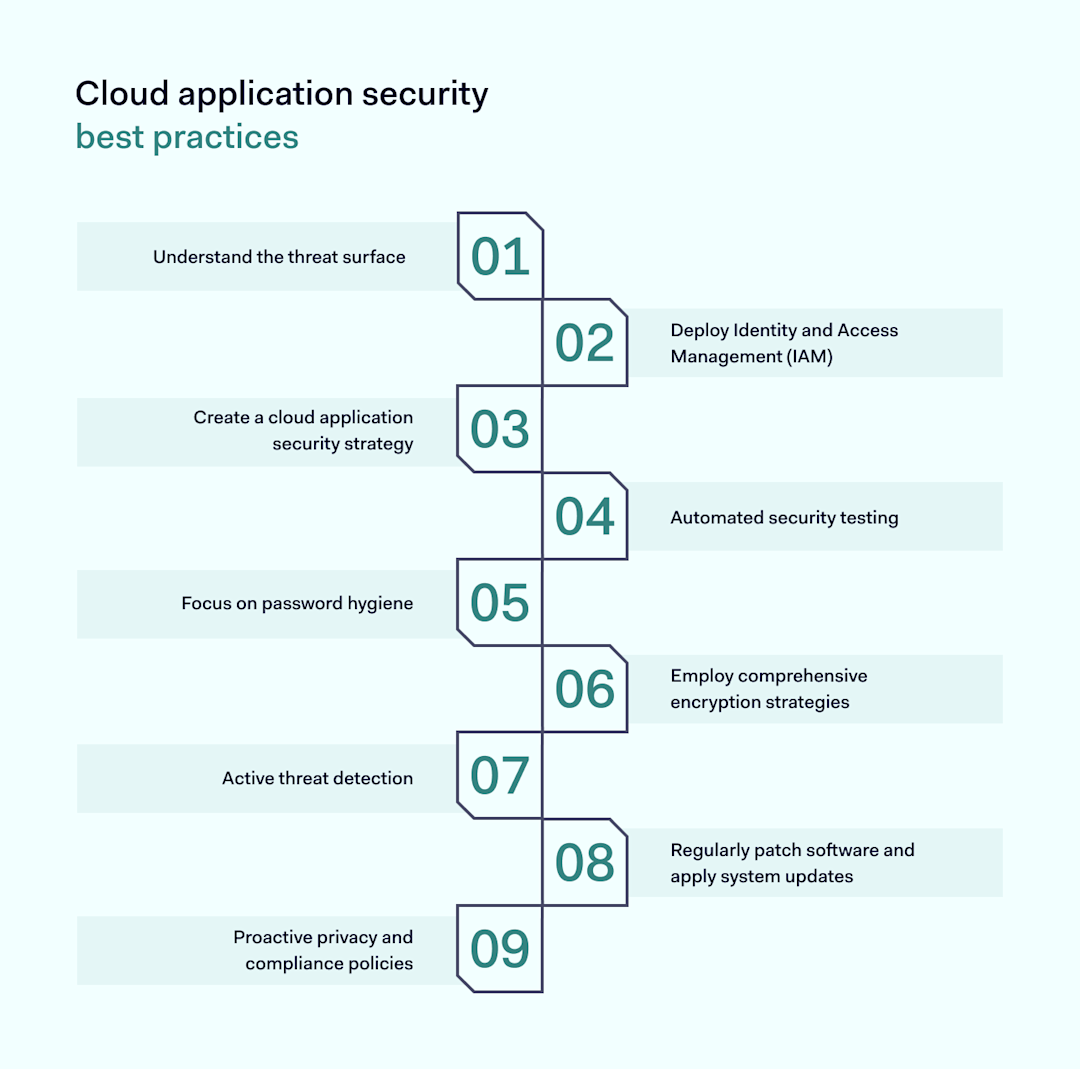
How To Build A Successful Cloud Security Strategy
How To Build A Successful Cloud Security Strategy - Learn to build a successful cloud strategy in 2024. Developing a formal cloud strategy document is essential for aligning. This guide covers essential steps, benefits, and steps to help you stay competitive and grow your business. Learn the new cloud security operating model and steps towards cloud security maturity. Cloud computing requires organizations to create a robust cloud security strategy that will protect their data, applications, and services in the cloud environment. In this article, we will guide you through the steps to create an effective cloud strategy document. This practical guide helps transform security teams and processes to remove risks. How to create a cloud. Whether you're interested in ethical hacking, incident response, cloud. That governance must also include advanced security measures to protect that data by guarding against security breaches and resolving any successful attacks quickly. Learn to build a successful cloud strategy in 2024. Developing a robust cloud security strategy requires a thorough understanding of the organization’s cloud environment, business objectives, and unique risk factors. This is backed by the trust of our millions of. Cloud security strategy involves implementing comprehensive measures to safeguard your data and applications in the cloud from threats and breaches. Successful cyber recovery requires more than just backup solutions; Whether you're interested in ethical hacking, incident response, cloud. Developing a formal cloud strategy document is essential for aligning. That governance must also include advanced security measures to protect that data by guarding against security breaches and resolving any successful attacks quickly. The field of cybersecurity is vast, with numerous job roles that cater to different skill sets and career goals. In this article, we explore key considerations for constructing a robust cloud security program and discuss how tools such as vulert vulnerability scanner can assist in managing. That governance must also include advanced security measures to protect that data by guarding against security breaches and resolving any successful attacks quickly. With the number of services and offerings from csps continuing to grow rapidly — especially new ai. Developing a robust cloud security strategy requires a thorough understanding of the organization’s cloud environment, business objectives, and unique risk. Learn the new cloud security operating model and steps towards cloud security maturity. Aws is architected to be the most secure global cloud infrastructure on which to build, migrate, and manage applications and workloads. This is backed by the trust of our millions of. In this article, we will guide you through the steps to create an effective cloud strategy. Learn and explore how to build a safe and proactive cloud security architecture for your organization with astra. The field of cybersecurity is vast, with numerous job roles that cater to different skill sets and career goals. Whether you're interested in ethical hacking, incident response, cloud. Learn the new cloud security operating model and steps towards cloud security maturity. It. This guide covers essential steps, benefits, and steps to help you stay competitive and grow your business. Audit domain controllers to log successful kerberos tgs requests and ensure the events are monitored for anomalous activity. Cloud computing requires organizations to create a robust cloud security strategy that will protect their data, applications, and services in the cloud environment. Learn the. That governance must also include advanced security measures to protect that data by guarding against security breaches and resolving any successful attacks quickly. Cloud security strategy involves implementing comprehensive measures to safeguard your data and applications in the cloud from threats and breaches. How to create a cloud. With the number of services and offerings from csps continuing to grow. June 19, 2020 | by: A cloud security strategy is the. Successful cyber recovery requires more than just backup solutions; This guide covers essential steps, benefits, and steps to help you stay competitive and grow your business. This practical guide helps transform security teams and processes to remove risks. Learn to build a successful cloud strategy in 2024. It demands a comprehensive, integrated approach that addresses all five s’s while maintaining the agility to. In this article, we explore key considerations for constructing a robust cloud security program and discuss how tools such as vulert vulnerability scanner can assist in managing. The field of cybersecurity is vast, with numerous. It demands a comprehensive, integrated approach that addresses all five s’s while maintaining the agility to. Learn and explore how to build a safe and proactive cloud security architecture for your organization with astra. Audit domain controllers to log successful kerberos tgs requests and ensure the events are monitored for anomalous activity. Whether you're interested in ethical hacking, incident response,. In this article, we explore key considerations for constructing a robust cloud security program and discuss how tools such as vulert vulnerability scanner can assist in managing. By converging application security, cloud security, and security operations into a unified strategy, organizations can eliminate blind spots and respond to threats faster. In this article, we will guide you through the steps. In this article, we explore key considerations for constructing a robust cloud security program and discuss how tools such as vulert vulnerability scanner can assist in managing. By converging application security, cloud security, and security operations into a unified strategy, organizations can eliminate blind spots and respond to threats faster. Cloud security strategy involves implementing comprehensive measures to safeguard your. By converging application security, cloud security, and security operations into a unified strategy, organizations can eliminate blind spots and respond to threats faster. This is backed by the trust of our millions of. How to create a cloud. Learn and explore how to build a safe and proactive cloud security architecture for your organization with astra. June 19, 2020 | by: Cloud computing requires organizations to create a robust cloud security strategy that will protect their data, applications, and services in the cloud environment. A cloud security strategy is the. Developing a formal cloud strategy document is essential for aligning. Most important is to first take ownership. Different cloud providers have strengths in different areas. Learn the new cloud security operating model and steps towards cloud security maturity. In this article, we explore key considerations for constructing a robust cloud security program and discuss how tools such as vulert vulnerability scanner can assist in managing. Learn how a strong cloud security strategy sets the foundation for cloud adoption, unleashing innovation. The field of cybersecurity is vast, with numerous job roles that cater to different skill sets and career goals. This guide covers essential steps, benefits, and steps to help you stay competitive and grow your business. Aws is architected to be the most secure global cloud infrastructure on which to build, migrate, and manage applications and workloads.Cloud application security guide NordLayer Blog
How to build a cloud security strategy that works Paramount’s cloud
Cloud Security Strategy Examples, Elements and Planning Scrut Automation
Cloud Security Strategy Building a Robust Policy in 2024
Learn the Importance of Cloud Security Strategy Solid System
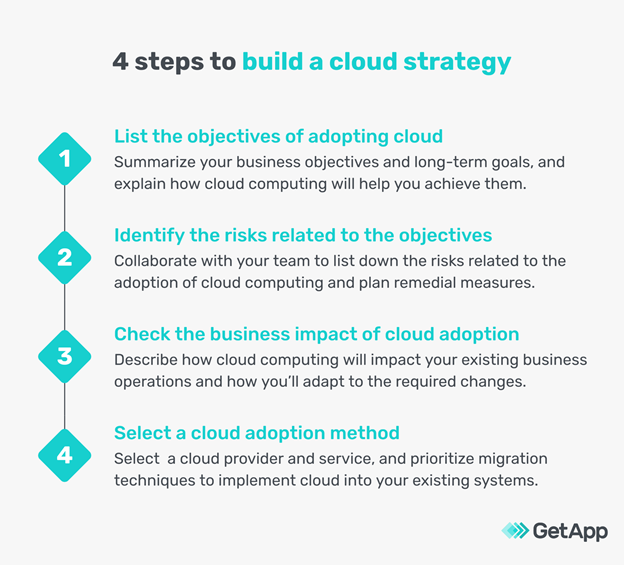
Startup Guide to Cloud How to Create a Cloud Strategy
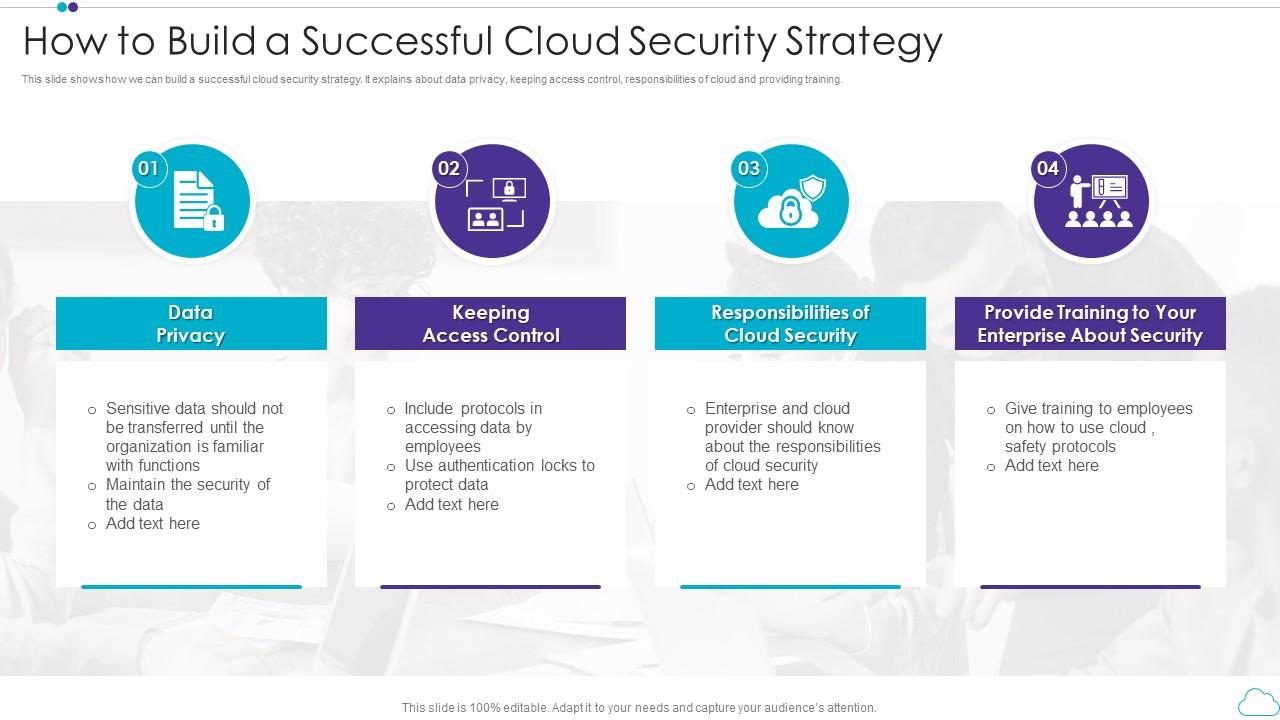
How To Build A Successful Cloud Security Strategy Presentation
How to Build a Successful Cloud Security Strategy
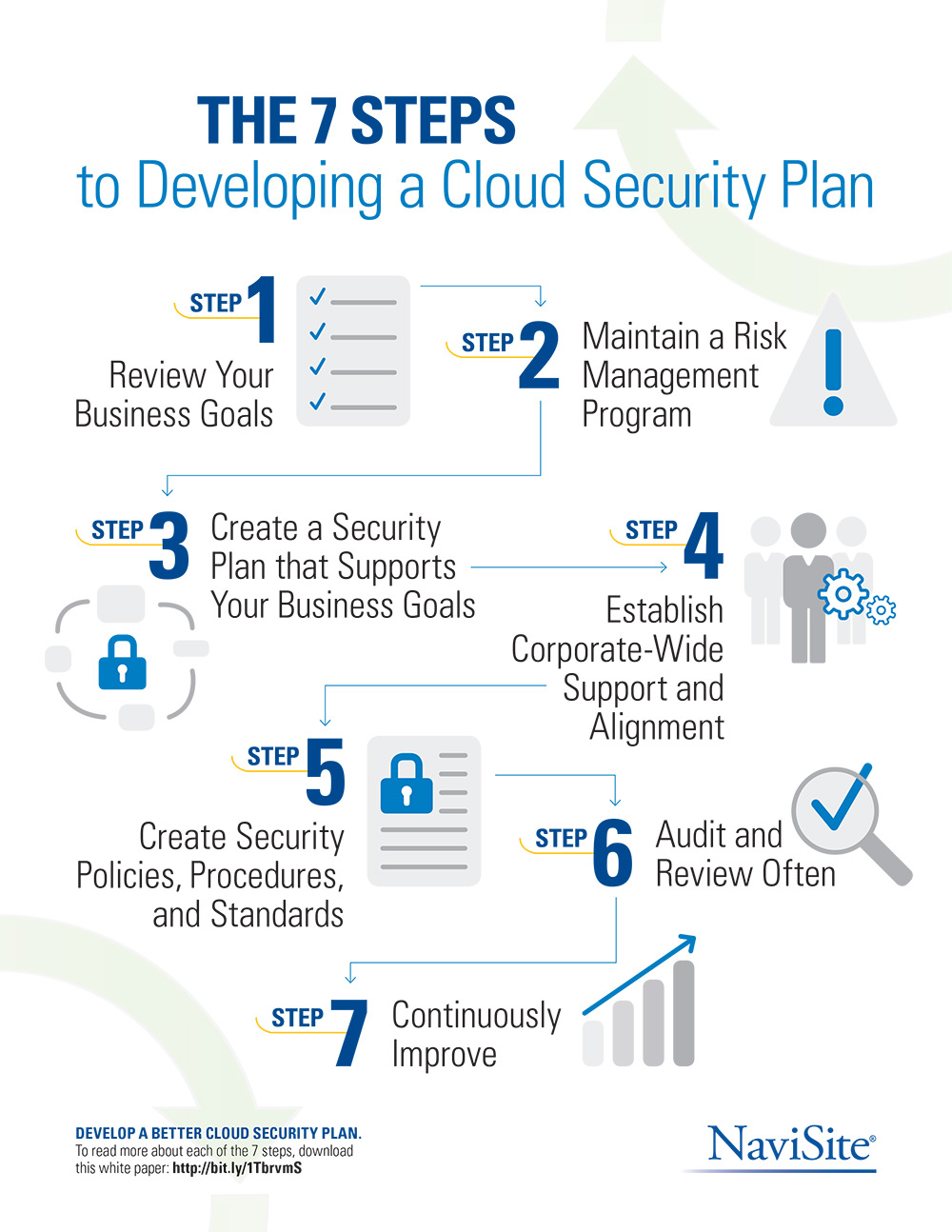
The 7 Steps to Developing a Cloud Security Plan Insight
Cloud Security Strategy Examples, Elements and Planning Scrut Automation
Successful Cyber Recovery Requires More Than Just Backup Solutions;
Cloud Security Strategy Involves Implementing Comprehensive Measures To Safeguard Your Data And Applications In The Cloud From Threats And Breaches.
Learn To Build A Successful Cloud Strategy In 2024.
It Demands A Comprehensive, Integrated Approach That Addresses All Five S’s While Maintaining The Agility To.
Related Post: