Itn Version 7 Building And Securing A Small Network Exam
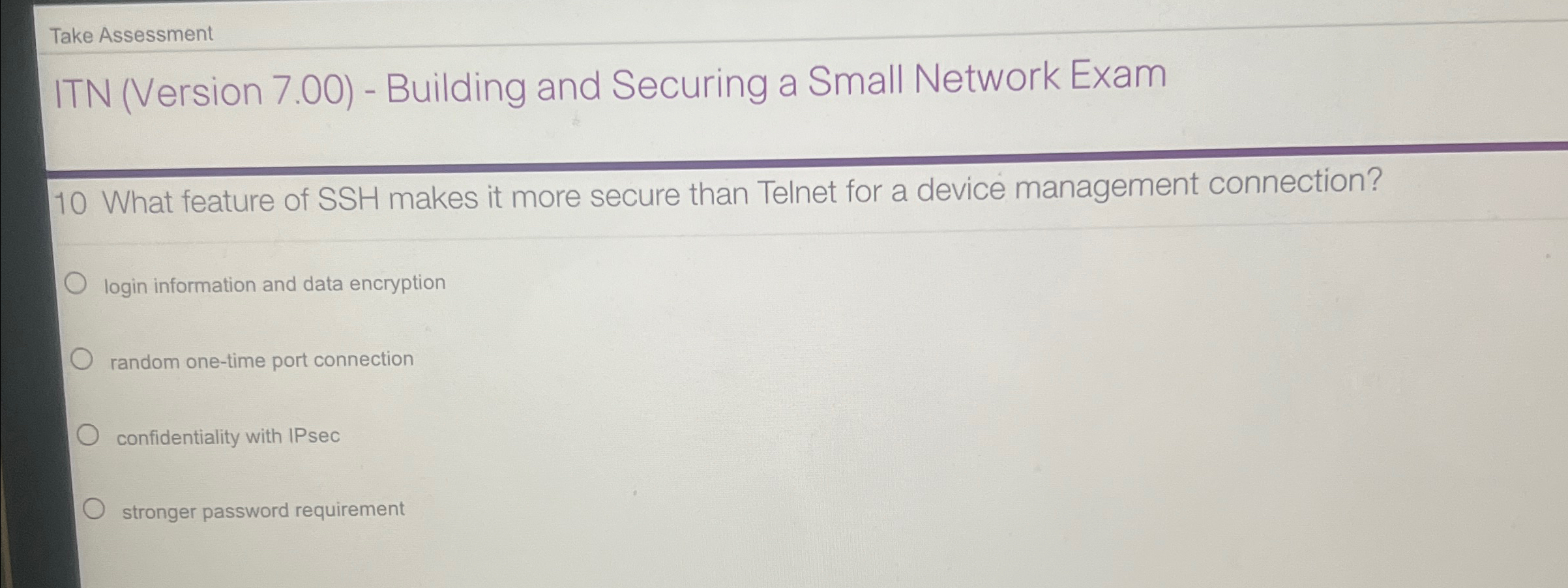
Itn Version 7 Building And Securing A Small Network Exam - Itn (version 7) building and securing a small network exam explanation: Quizlet has study tools to help you learn anything. Not the question you’re looking for? 1 0 what feature of ssh makes it more secure than telnet for a device management connection? [to require users to prove who they are [to determine which resources a user can access [to keep track of the actions of. Here’s the best way to solve it. Post any question and get expert help quickly. Which protocol would be best to use to securely access. Improve your grades and reach. Here’s the best way to solve it. 1 0 what feature of ssh makes it more secure than telnet for a device management connection? Which protocol would be best to use to securely access. Which component is designed to protect against unauthorized communications to and from a computer? Itn (version 7) building and securing a small network exam explanation: A user is redesigning a network for a small company and wants to ensure security at a reasonable price. The login and password cisco commands are used with telnet switch configuration, not ssh configuration. What is the purpose of the network security authentication function? Post any question and get expert help quickly. Not the question you’re looking for? Post any question and get expert help quickly. [to require users to prove who they are [to determine which resources a user can access [to keep track of the actions of. Here’s the best way to solve it. Which protocol would be best to use to securely access. Post any question and get expert help quickly. Here’s the best way to solve it. Here’s the best way to solve it. The login and password cisco commands are used with telnet switch configuration, not ssh configuration. Itn (version 7) building and securing a small network exam explanation: Here’s the best way to solve it. Network security fundamentals & build a small network learn with flashcards, games, and more — for free. Not the question you’re looking for? Post any question and get expert help quickly. What is the purpose of the network security authentication function? Network security fundamentals & build a small network learn with flashcards, games, and more — for free. Post any question and get expert help quickly. Network security fundamentals & build a small network learn with flashcards, games, and more — for free. Here’s the best way to solve it. The login and password cisco commands are used with telnet switch configuration, not ssh configuration. Post any question and get expert help quickly. Not the question you’re looking for? Here’s the best way to solve it. The login and password cisco commands are used with telnet switch configuration, not ssh configuration. What is the purpose of the network security authentication function? Post any question and get expert help quickly. Itn (version 7) building and securing a small network exam explanation: This command displays the rou. Post any question and get expert help quickly. Network security fundamentals & build a small network learn with flashcards, games, and more — for free. The login and password cisco commands are used with telnet switch configuration, not ssh configuration. Not the question you’re looking for? Post any question and get expert help quickly. This command displays the rou. Improve your grades and reach. Quizlet has study tools to help you learn anything. A user is redesigning a network for a small company and wants to ensure security at a reasonable price. Not the question you’re looking for? [to require users to prove who they are [to determine which resources a user can access [to keep track of the actions of. Quizlet has study tools to help you learn anything. Here’s the best way to solve it. Here’s the best way to solve it. Not the question you’re looking for? Which protocol would be best to use to securely access. Here’s the best way to solve it. Improve your grades and reach. What is the purpose of the network security authentication function? Which protocol would be best to use to securely access. Here’s the best way to solve it. Which component is designed to protect against unauthorized communications to and from a computer? Here’s the best way to solve it. Network security fundamentals & build a small network learn with flashcards, games, and more — for free. Not the question you’re looking for? What is the purpose of the network security authentication function? Improve your grades and reach. Not the question you’re looking for? A user is redesigning a network for a small company and wants to ensure security at a reasonable price. Post any question and get expert help quickly. 1 0 what feature of ssh makes it more secure than telnet for a device management connection? The login and password cisco commands are used with telnet switch configuration, not ssh configuration. [to require users to prove who they are [to determine which resources a user can access [to keep track of the actions of. Post any question and get expert help quickly.CCNA 1 v7 ITN v7.02 Modules 1617 Exam Answers 2023 100
CCNA1 v7 ITNv7 Modules 16 17 Building and Securing a Small
Solved ITN (Version 7.00) Building and Securing a Small
Solved ITN (Version 7.00) Building and Securing a Small
Solved ITN (Version 7.00) Building and Securing a Small
Solved Take AssessmentITN (Version 7.00) Building and
Solved ITN (Version 7.00) Building and Securing a Small
CCNA 1 ITN 7.02 Modules 16 17 Building and Securing a Small Network
CCNA Module 1617 Test Answers / ITN (Version 7.00) Building and
Here’s The Best Way To Solve It.
Quizlet Has Study Tools To Help You Learn Anything.
This Command Displays The Rou.
Itn (Version 7) Building And Securing A Small Network Exam Explanation:
Related Post: